Tuesday, June 15, 2010
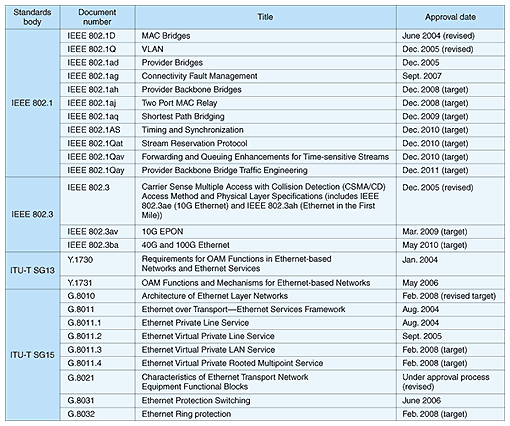
Provider Bridges
Amendment to 802.1Q, for the purpose to create an architecture and bridge protocols to provide separate instances of MAC services to multiple independent users of a Bridged Local Area Network without the cooperation of the users, and small cooperation between users and provider of the MAC service.
What this does is provides the possibility for customers to run their own VLANs inside a service provider's provided VLAN. In doing this the Service provider makes one VLAN for the customer and the customer creates the given VLAN as a trunk.
Wednesday, June 9, 2010
CR-LDP and RSVP-TE
There are many similarities between CR-LSP and RSVP-TE for constraint-based routing. The Explicit Route Objects that are used are extremely similar. Both protocols use ordered Label Switched Path (LSP) setup procedures. Both protocols include some QoS information in the signaling messages to enable resource allocation and LSP establishment to take place automatically.
At the present time CD-LDP development has ended and RSVP-TE has emerged as the "winner" for traffic engineering protocols.
IS-IS
A protocol used to determine the best way to forward datagrams through a packet switched network.
- A IGP protocol
- Not intended for routing between ASes
- Floods topology information throughout the network
- Packets are forwarded based on best topological path through network
- Uses Dijkstra's Algorithm
- Preferable to service providers while OSPF is preferable to enterprise networks
Because both are link state, both support Classless networks, use multicast to discover neighboring routers using hello packets, and support authentication of routing updates, these protocols are very similar.
- OSPF routes IP and is a layer 3 protocol (on IP), IS-IS is an OSI protocol (same as CLNS), and does not use IP to carry routing information.
- A topological map is built of the network, which indicate which IP subnets each IS-IS router can reach, using the lowest cost to an IP subnet to forward traffic.
- Differs from OSPF in how topology is flooded. It is less chatty, and can support larger networks, therefore favorable in ISP (Internet Service Provider) networks. It easily adaptive to support IPV6 due to the fact its neutral regarding network address routing.
- The "Area" concept is different - IS-IS routers use Levels, with Level 1 being and intra (within) area, Level 2 being an inter (between) area, or level 1 and 2 routers. Level 2 routers can only form relationships with other level 2 routers, and level 1 with level 1. 1-2 routers exchange with both kinds and are used for the communication between the two. IS-IS borders are in between routers, designated as level 2 or 1-2. This results in a IS-IS router being a part of a single area, and does not require area 0. OSPF creates a web topology and IS-IS creates a logical topology of a backbone or level 2 routers with branches of level 1-2 and level 1 routers forming individual routers.
Tuesday, June 8, 2010
OSPF
- Dynamic routing protocol in IP networking. A link state routing protocol in the group of Interior gateway protocols (IGP), that operates in a single Autonomous system (AS). IPV4 uses OSPF V2
- Gathers link state information from routers and constructs topology map of the network, this creates the routing table
- Supports variable-length subnet masking (VLSM) or CIDR
- Detects changes in topology and converges a new routing structure within seconds using a shortest path algorithm (Dijkstra's)
- Link state info is maintained on each router as a link state database (LSDB), making a tree image of the network. Copies of this are updated through flooding on OSPF routers
- Routing policies in OSPF are governed by link cost factors, this could be the distance (round trip time), network throughput of the link, or link availability and reliability, represented as unitless numbers. Load balancing can occur with traffic balancing between equal path costs.
- OSPF networks can be divided into areas, which are identified as 32-bit numbers, in decimal or octet.
- Area 0 (0.0.0.0) is the core or backbone region. Each additional area must have a direct or virtual connection to the backbone, these connections are maintained by a area border router (ABR). ABRs maintains separate link state databases for each area it serves and contains summarized routes for all areas in the network.
- OSPF doesn't use a TCP/IP protocol (UDP or TCP), but is encapsulated into IP datagrams with port number 89.
- OSPF uses multicast addressing for route flooding on broadcast network links, id a non-broadcast network exists special provisions allow neighbor discovery. OSPF IP packets never travel more than 1 hop, OSPF reserves the multicast address 224.0.0.5.
- When multicast IP traffic needs to be routed, OSPF supports Multicast Open Shortest Path First (MOSPF), this is not used all the time as PIM is typically used in conjunction with OSPF or other IGPs are widely deployed.
- OSPF can run securely between routers, using a variety of authentication methods to allow only trusted routers.
- Version 3 (for IPV6) does not use authentication, instead it used IPSec, It runs per link, rather than subnet. IP prefix's has been removed from hello and link state adverts, area and router ID are still 32-bit values.
- Adjacent routers are formed when they are in the same broadcast domain or have a point to point link. This is identified by a hello OSPF packet, and a two-way state is formed (very basic). The routers in the network select a designated router (DR) and a backup designated router (BDR) which act as a hub to reduce traffic. OSPF uses unicast and multicast to send hello's and link state updates.
- Neighbor tables are called adjacency databases. In order to form neighbor relationships between two routers, the interfaces must be in the same area, one interface can only belong to one area.
- Backbone is responsible for distributing info to non-backbone areas, and must be contiguous. If physical limitations exist, the configuration of virtual links can be used. As an example - 0.0.0.0 is physically connected to 0.0.0.1, 0.0.0.2 is not connected to .0 but it is connected to .1; .2 can use a virtual link through a transit area of .1 to reach the backbone.
- Stub area - does not receive route adverts external to the AS and routing within the area is based on a default route.
- Not so stubby area (NSSA)- A type of stub area that imports AS external routes and sends them to other areas, yet it itself (its own AS) does not receive AS external routes from other areas. In other words, its an injection of external routes in a limited fashion into the stub area.
- Totally stubby area (TSA) - Like a stub area, but does not allow summary routes in addition to not having external routes, or Inter-area (IA) routes are not summarizes into totally stubby area. Only default routes are used in the area, thus being the only Type 3 LSA in the area.
- NSSA TSA - Takes attributes of a TSA (Type 3 and 4 summary routs are not flooded into the area type). The area can receive only from the default route 0.0.0.0 but also contains the ASBR that accepts external routing info and injects it into the local area 0.0.0.0. LSA type 7 only exists in NSSA, the ASBR generates the LSA, and an ABR translated it into a type 5 LSA which is then propagated into the OSPF domain.
Path Preference:
Path cost is used as a basic routing metric, determined by speed of the interface. There are 4 types of metrics, with preference in order:
1.Intra-area
2.Inter-area
3.External type 1 - external path cost and sum of internal path cost to ASBR
4.External Type 2 - value of external path cost
OSPF-TE:
Traffic engineering uses opaque LSA type-length-value elements to obtain more information about topology. This can support OOB on data plane network, and can be used on non-IP, such as Optical networks.
Router Types:
The router type is an attribute of an OSPF process. A physical router can have one or more OSPF process - ex) A router connected to more than one area and receives routes from a BGP process connected to another AS, is both a ABR and an ASBR
Designated router: Router interface elected to be broadcast multiaccess. Nonbroadcast multiaccess (NBMA) media would require special techniques to support DR function, this is usually done via point to point lines.
- Area Border Router (ABR): A router that connects one or more areas to the main backbone. Its a member of all areas its connected to, and keeps a link state DB in memory, one for each area its connected
- Autonomous System Boundary Router (ASBR): A router that's connected to more than one routing protocol and exchanges routing information with other routers in other protocols. They typically run an exterior routing protocol like BGP. It is used to distribute routes from other external ASs throughout its own AS.
- Internal Router: A router that has OSPF neighbor relationships interfaces in the same area.
- Backbone router: Routers connected to the OSPF backbone.
DRs can be associated with other OSPF router types, A router can have a physical interface that are DR, others Backup (BDR), and others non-designated. DRs are elected on the following criteria:
- If priority on OSPF is 0, it will never be DR or BDR
- If DR fails and BDR takes over, another election will choose a new BDR
- Highest priority hello packets win the election.
- If two routers tie in priority setting, the highest Router ID (RID) wins (highest loopback IP configured on the router). If no loopback exists the highest interface IP wins.
- Second highest priority becomes BDR
- priority is between 0-255, higher numbers increase chances of becoming DR
- If a new router with a higher priority comes online after a DR has been elected, it will not be a DR until current DR fails.
- When DR goes down and BDR takes over, a new BDR is elected. If the scenario repeats the new BDR stays unchanged.
DRs are a source for routing updates, they maintain a complete topology table of the network and send multicast updates. All routers form a slave/master relationship with the DR. When updates are received they are sent to the DR and BDR on 224.0.0.6, and DR sends and update on 224.0.0.5. This reduces network load. Elections on NBMA (Frame Relay or ATM) can also occur. elections do not happen on p-to-p links because the routers must be adjacent and the bandwidth cannot be further optimized.
There are 5 OSPF Packet formats as follows:
Type Description 1 Hello 2 Database Description 3 Link State Request 4 Link State Update 5 Link State Acknowledgement
Monday, June 7, 2010
MPLS
- When used in a network, incoming packets are assigned a "Label" by a Label Edge Router (LER). The packets are forwarded along a Label Switch Path (LSP), by a Label Switch Router (LSR) makes the forwarding decisions, wherein the LSR strips off the label and applies a new one with instructions for the next hop on how to forward the packet.
- LSPs are similar to circuit switched paths, except they are not dependent on particular layer 2 technology.
- LSPs can traverse any type of transport medium (ATM, Frame Relay or Ethernet)
- Brings the speed of layer 2 switching to layer 3, routers preform forwarding decisions based on the label, rather than route lookup. Although now irrelevant due to routers able to process routing information as fast speeds now.
- Class of traffic and path engineering
- Service providers create IP tunnels throughout their network (VPNs) without the need for encryption or end user appliances
- L2 Transport (Ethernet, Frame relay and ATM over IP/MPLS core)
- Elimination of multiple layers, all L1 (SONET), L2 (ATM) to L3, thereby simplifying the network management.
Label: Short, fixed length, locally significant ID used to identify a FEC (Forwarding Equivalence Class) to which that packet is assigned.
- The MPLS Label is formatted as follows:
|-20bits Label-|-3bits CoS-|-1bit Stack-|-8bits TTL-|
- 20-bit label field - Value of the MPLS label
- 3-bit COS field for queuing and discard algorythms
- 1-bit stack field - hierarchical label stack
- 8-bit Time to live (TTL) or shim header, provides IP TTL functionality.
- Provisioned using Label Distribution Protocols (LDPs) such as RSVP-TE or CR-LDP - these are used to establish a path through the network and reserve necessary resources to meet pre-defined service requirements.
- Contrasted with traffic trunks - The path which a trunk traverses can be changed, the traffic trunk are aggregations of traffic flows of the same class inside an LSP
- Lets an LSR distribute labels to LDP peers. When a label is assigned to a Forwarding Equivalence Class (FEC), LDP lets is relevant peers know of the label and its meaning. When a path is made, LDP helps in establishing a LSP using a set of procedures to distribute these labels among LSRs.
- LSRs will agree on what labels should be used to forward traffic, this understanding is agreed upon by Label Distribution. LDP and Labels are the foundation of label switching.
LDP has the following basic characteristics:
- Provides LSR discovery mechanism which allows peer discovery and communication establishment
- Four classes of the message exist: DISCOVERY, ADJACENCY, LABEL ADVERTISEMENT, and NOTIFICATION
- Runs over TCP
- Unsolicited downstream vs downstream on demand label assignment
- Order vs independent LSP
- Liberal vs Conservative label retention
- A set of packets which are forwarded in the same manner.
- FEC packets follow the same path
- FEC packets are identified by labels
- Examples include unicast packets, and multicast packets with the same source and destination address. Another example is when unicast Type of Service (TOS) bits are the same.
A set of LSRs that packets belonging to a particular FEC travel to reach their destination. Because of the hierarchy label, it is possible to have different LSPs at different levels of labels for a packet to reach the destination - A LSP with a label of x has a set of LSRs that has a packet p that has to travel at x to reach its destination
As an example: consider the following scenario
|------| 1 1 |-----|
| R1 |--\ /---| R5 |
|------| \ 2 2 2 / |-----|
\|------| |-----| |-----| /
| R2 |---| R3 |---| R4 |/
|------| |-----| |-----|
p must travel from R1 to R5, 1 and 2 are the stack depth. R1 and 5 are edge routers and the rest are interior gateway routers. R1 and 5 are peers, alternately 2,3, and 4 are peers. R1 will swap p's label with a corresponding label used by R5, it will also push a new label for R2,3, and4 with the stack level at 2. Two LSPs exist - 1 at R1 and 5, 2 at R2,3, and 4.
- Routing protocols and routes learned from the LSRs build LSPs. RSVP may be used
- Possible to support both ordered and independent control without interoperability
- Label binding can be created locally and remotely - downstream or upstream LSRs. Created in response to control or data driven traffic, the binding controlled in a stand alone protocol or piggybacking from an existing one such as Border Gateway Protocol (BGP).
IGPs like OSPF and IS-IS are used to define reachability and binding/mapping between FEC and next hop addresses. No changes are required to run MPLS in corporations that use these IGPs due to the compatibility with these protocols.
Supported Protocols:
Network layer - IPV6, IPV4, IPX, and Appletalk
Link Layer - Ethernet, Token Ring, FDDI, ATM, Frame Relay, and Point to point.
MPLS not only works over any data link layer protocol, but carries a data link layer protocol over IP, Enabling Ethernet over MPLS
MPLS and ATM:
ATM can have traffic engineering capabilities with MPLS. This is done by tagging IP packets with labels that specify routes and priorities. This combines routing scalability and flexibility with the performance and traffic management of layer 2 switching.
Can map IP addresses and routing info into ATM switching tables. MPLS uses the same label swapping method as ATM. ATM-LSRs are forwarded by ATM forwarding component with label info in ATM header (VCI and VPI Fields). MPLS provides control component for IP on ATM switches and routers, MPLS IP services replace PNNI, ATM ARP Server, and NHRP Server.
Sometimes MPLS and ATM are on the same device, but they will run separately. MPLS path changes have no effect on ATM VCs(Virtual Circuits), this is called Ships in the Night. ATM control mechanisms can avoid resource conflicts by not allowing reservation of resources imposed by MPLS. This is being used to slowly phase out ATM and understand the need of resources to fill be MPLS.
MPLS-TE:
MPLS Traffic Engineering is used to select the best paths on the network when multiple or parallel links exist. It also optimises network resources for traffic performance.
In order to support TE, Source routing and the following components are needed:
- All constraints are taken into account, therefore the source needs to know the restrictions of the other routers in the network
- Ability to determine information about topology and attributes with links in network once path is established, forwarding support is necessary
- Ability to reserve network resources and modify link attributes
MPLS TE leverages several foundation technologies:
- Constraint Shortest path first algorithm used in path calc - Modified version of SPF algorithm for constrains support
- Extension of RSVP for forwarding state along path, also reserving resources
- IGPs link state and extension (OSPF with Opaque LSAs, IS-IS with Link State Packets TLV (type, length, and Value)) and keeping track of topology changes.
FECs play an important role here, if traffic is ingress in an MPLS domain a FEC can be handled equivalently when forwarding and can contain a single label. If traffic is bound to the same FEC, the traffic will be forwarded the same way, regardless of network layer headers.
MPLS and loops:
Loop handling can be split between:
- Loop prevention (Path Vector)
- Loop mitigation - minimize negative effect of loops (TTL). When TTL reaches 0 the packet is discarded
- Dynamic routing protocols
If TTL still cannot be used, hop count can, like TTL it will decrement by 1 for every successful label binding. This information is carried within Link Description Protocol messages.
Path Vector has a list of LSRs that label distribution control message has traversed. Each LSR adds its info to the path vector list, when a LSR receives a message from its own identifier a loop is detected (this is also used by BGP with AS path attribute).
2 or more ASes within the same MPLS domain:
If two adjacent ASes exist, via ASBR summarizing eBGP routes before distributing them to their IGP or IGP routes covering a set of FECs which are different than eBGP routes, then ASBRs cannot forward traffic based on top-level label. This also applies with TE tunnels. Some traffic will be forwarded based on IP or a non top level label.
Now we have 2-3 MPLS forwarding domains with multiple ASes - one for each AS and one for a link between two ASBRs (where labeled packets are used instead of IP packets are used).
ASBRs probably would not be a ATM-LSR, due to the limited capacity of manipulating label stacks or forwarding unlabeled IP traffic.
Also with multi-provider BGP+MPLS VPNs - no top level LSP are established therefore the two ASes are separate admin domains or the two providers agree to allow lower lever LSPs to be established across the two ASes.
MPLS VPNs:
MPLS for VPNs provide traffic isolation, like ATM or Frame Relay. MPLS does not encrypt traffic, IPsec would have to be employed.
BGP MPLS-VPNs can exist, wherein BGP propagates VPN-IPV4 info using BGP multiprotocol extensions (MP-BGP) for handling these extended addresses. Reachability info such as VPN-IPV4 addresses on Edge label switch routers are propagated, also reachability into for a given VPN is propagated only to other members of that VPN. BGP multiprotocol extensions identify valid recipients for VPN routing info. All VPN members learn routes to other members.
Another idea is to use separate routing tables for VPNs that do not involve BGP.
Layer 2 ecapsulation methods can be used for encapsulation methods and layer 2 transport signal mechanisms, this is known as the "Martini Draft". This would have an advantage to many service providers due to the multitude of services provided.
Layer 2 VPN:
These are layer 2 services such as Frame Relay, ATM and Ethernet over an IP/MPLS backbone. This simplifies networks and reduces expenses.
VPLS:
These are Ethernet VLANS using MPLS. All edge devices maintain MAC address tables for reachable end nodes, like how LAN switches do. They allow Ethernet Reachability across geographic distances served by MPLS services.
There is no ecryption across MPLS VPNs, instead the use of tags are important. This makes MPLS just as secure as ATM and Frame Relay as interception of these types of network would require access to the SP. If security is an issue, IPSec or SSL can be used before going on the wire.QOS:
MPLS Quality of Service is the same a IP - IP precedence, Committed access rate (CAR), Random Early Detection (RED), Weighted RED, Weighted Fair Queing (WFQ), Class-based WFQ, and priority Queing.
Diffserv has 64 classes, MPLS shim has 8, the exp field is 3 bits long and the diffsev us 6. Label-LSP and Exp-LSP solve this, since diffserv defines the interpretation of the TOS bits - as long as IP orecidence bits map to the Exp bits the same interpretation as the diffserv model can be applied to these bits. when extra bits are used L-LSP uses drop priority to identify what the remaining 3 bits mean.
The followings classes may be more appropriate for the initial deployment of MPLS QoS:
-
High-priority, low-latency "Premium" class (Gold Service)
-
Guaranteed-delivery "Mission-Critical" class (Silver Service)
-
Low-priority "Best-Effort" class (Bronze Service)
GMPLS:
- Encompasses time-divsion, wavelength, and spatial switching. Allows MPLS to be used as a control mechanism for configuring packet and not packet based devices.
- Introduces new protocol called Link Management Protocol (LMP). This runs between adjacent nodes and establishes control channel connectivity and failure detection, also verifies channel connectivity.
- Link Building - Grouping of many physical links into a single link
- Link Hierarchy - Issuing of a suite of labels for various requirements of physical and logical devices on a path.
- Unnumbered links - ability to config paths without IP info on every interface
- Constraint Based Routing - automatically provision additional bandwidth, or change forwarding behavior due to network conditions like congestion or requirements of additional bandwidth
Overlay is when optical and IP layers are separated with minimal interaction. An example of this today would be like ATM and IP, where there are no direct connections between the two routing layers.
Peer is simpler and more scalable, but overlay has fault isolation and separate control mechanisms for devices.
Friday, June 4, 2010
VRRP
- Consists of Master and backups, whereby the master does all the routing a a given point of time
- Uses 00-00-5E-00-01-XX as it's MAC address, with XX being its Virtual Router ID (VRID). The physical routers in a Virtual Router communicate within themselves using packets with Multicast IP of 224.0.0.18, port 112.
- The routers use a priority method to determine the master, highest priority wins, numbers are allocated between 1-255. This can and should be administratively set when planning a master swap in order to bypass hold time expiration timers (3xAdvertisment + skew time).
- If a backup router fails to receive a packet from the master router three times, the backup will assume connectivity to the master is down and and election process is started throughout the group of routers with multicast packets.
- Backup routers should only send multicast packets during elections, if all backup routers have the same priority, the router with the highest IP will become the master.
- Orderly Election time is made effective by the use of skew time (Skew time = 1-(priority/256)) This reduces the chance of a Thundering herd issue.
- If load sharing is used, backup router utilization is improved
R-PVST
- Cisco
- A combination of RSTP and PVST, much faster than PVST as it uses old STP (802.1d), thereby increasing the time it takes for fail over (50 seconds).